
What Is the L2TP VPN Protocol? Layer 2 Tunneling Protocol Explained in 2025
- Table of Contents
- Meaning: What Is L2TP?
- L2TP Protocols & Components
- How Does L2TP Work?
- Layer 2 Tunneling Protocol (L2TP) Features
- What Is L2TP Used For?
- What Is L2TP Passthrough?
- What Does L2TP Use for Encryption?
- L2TP VPN Pros and Cons
- How Does L2TP Differ From Other VPN Protocols?
- Conclusion
- FAQ: L2TP VPN Security
What Is the L2TP VPN Protocol?
L2TP is a VPN protocol that provides secure connections when paired with IPsec, and it’s compatible with Windows, Linux, macOS, Android, iOS and routers. It’s one of the most cost-effective VPN protocols, which is why it’s used for remote access.
With so many VPN protocols available, it’s easy to get confused about how each one works. One example that many VPN users may find obscure is the Layer 2 Tunneling Protocol (L2TP). Today, I’ll answer the question, “What is L2TP VPN?” and explain why some of the best VPNs are still using this protocol.
Compared to widely used protocols like WireGuard, OpenVPN and IKEv2, L2TP is a little outdated. Created over 20 years ago, it was one of the first VPN protocols. However, it’s still usable — and useful — due to some features and capabilities that go beyond regular VPN protocols.
This article will cover the meaning of L2TP, along with its protocols, components and features. We’ll discuss how it works and what it’s used for, and we’ll explore its strengths and weaknesses. Read on if you want to crack open the L2TP mystery. We’ve also got a whole article on VPN protocols that provides key background information.
Meaning: What Is L2TP?
L2TP is an acronym for Layer 2 Tunneling Protocol, a VPN protocol that creates a connection between devices and VPN servers without encryption. Cisco and Microsoft developed it over two decades ago to replace the Point-to-Point Tunneling Protocol (PPTP).
The world switched from PPTP to L2TP because L2TP supports tunneling over different media, while PPTP is limited to tunnels over IP. Additionally, PPTP supports one tunnel between endpoints, but L2TP can work with multiple tunnels. In short, L2TP was a vast improvement over PPTP on all types of VPNs.
L2TP isn’t widely used today. There are better options like Secure Socket Tunneling Protocol (SSTP) and OpenVPN. Some VPN services, like ExpressVPN and CyberGhost, have even discontinued L2TP support — see our ExpressVPN review and CyberGhost review to learn what they offer instead.
When L2TP is used, it’s usually paired with the Internet Protocol Security (IPsec) suite, which provides data integrity checks and authentication. That’s how we get L2TP/IPsec, where IPsec handles the creation of a secure channel for encapsulating L2TP traffic. IPsec supports different types of encryption, including AES 256-bit — one of the most secure ciphers.
L2TP Protocols & Components

Since the L2TP protocol lacks native encryption, it must be combined with other components and protocols to compensate for it. When Microsoft and Cisco collaborated to make L2TP usable and secure, they integrated features from other tunneling protocols.
L2TP uses Microsoft’s PPTP to work with dial-up networks, and it uses Cisco’s Layer 2 Forwarding to establish secure connections over the internet and IP-based networks.
L2TP also adds two key components. The first is L2TP Access Concentrator (LAC), which receives packets from a remote client and forwards them to the second component, L2TP Network Server (LNS). LNS is the termination and authentication point for Point-to-Point Protocol (PPP) streams.
PPP is a data link layer protocol that facilitates communication between devices that can’t transmit IP packets. For example, ISPs used PPP to give customers dial-up internet access over phone networks. In the case of L2TP, PPP acts as the gateway that allows encrypted traffic to access necessary network assets.
How Does L2TP Work?
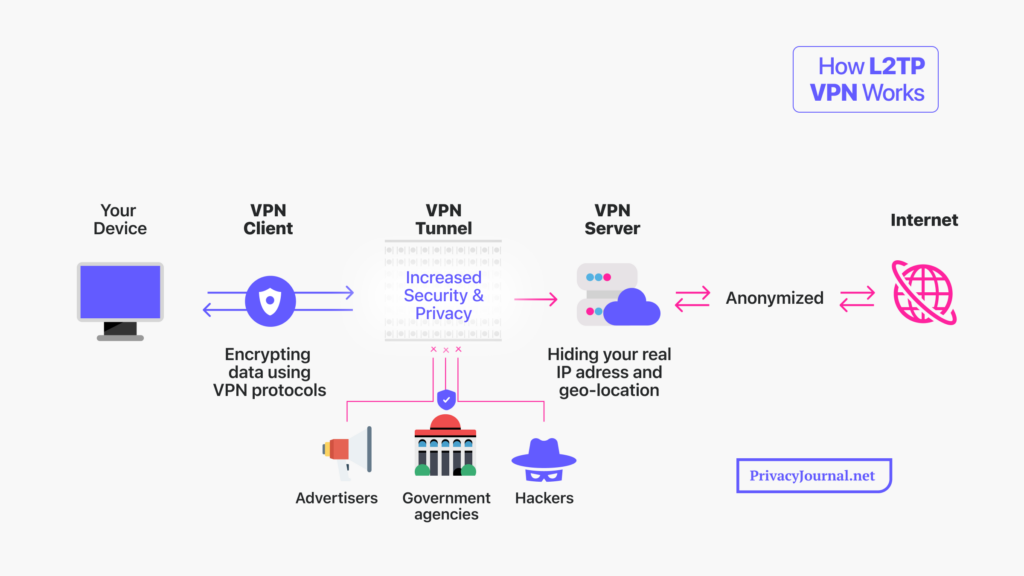
- L2TP establishes a connection between your device and the VPN server you intend to use. It combines with IPsec to create a secure tunnel between the LNS and LAC endpoints through which data is transmitted.
- The LNS and LAC negotiate their relationship and assign IP addresses to all the devices in the chain before any data transmission occurs.
- With the endpoints clearly defined, the data being sent through this tunnel is broken into packets. L2TP enables a PPP link layer for encapsulating data packets, preparing them for transfer.
- The L2TP packets are transferred over the internet.
- When they reach the other endpoint — the VPN server — L2TP unpacks these encapsulated packets, and IPsec immediately decrypts them. This restores the packets to their original readable format and makes them accessible on the local area network linked to the VPN server.
What Is L2TP Over IPsec?
L2TP Over IPsec (L2TP/IPsec) is what you get when you combine Layer 2 Tunneling Protocol with IPsec — a Layer 3 authentication and encryption protocol. This protects any transmitted traffic against external interference, which isn’t possible with L2TP alone.
Layer 2 Tunneling Protocol (L2TP) Features
The following are some key features that have allowed L2TP to remain relevant.
- Support for multiple protocols: L2TP is a highly versatile VPN communication protocol that works seamlessly with a host of different security protocols like IPsec. Its ability to work with new security technology is one reason why L2TP has lasted so long.
- High compatibility: L2TP is compatible with widely used operating systems like macOS, Windows, Linux, Android, iOS and some routers. For a largely outdated protocol, this is quite impressive.
- Solid security: When combined with IPsec, L2TP provides AES 256-bit encryption, which is very hard to breach and prevents external parties from intercepting the data transmitted between endpoints.
- PPP integration: L2TP remains vital for networks that still use PPP. Since PPP is also outdated, L2TP/IPsec is one of the only protocols that can integrate with it. L2TP can extend PPP to support encryption, authentication, data compression and more.
- Support for voluntary and compulsory tunneling: The VPN user initiates voluntary tunneling, while the network carrier initiates compulsory tunneling. Voluntary tunneling can be used to bypass firewalls. Compulsory tunneling can enforce network policies, like routing all traffic through a secure tunnel.
- Cost-effectiveness: When securing remote access networks for corporations that use VPNs, L2TP reduces the dial-up costs and overheads. With L2TP, you don’t have to set up individual connections at each access point — all traffic can be routed securely through a single point.
What Is L2TP Used For?
L2TP’s original purpose was to replace remote network dial-up connections to save on costs. Over time, people have found many uses for L2TP, including the following:
L2TP as a VPN
As mentioned, L2TP allows you to connect to a private server. When combined with IPsec, it’s regarded as a reliable protocol, ensuring that your VPN is safe enough to protect your online traffic.
L2TP/IPsec VPN tunnels are especially effective for remote access networks. They securely connect employees to their central offices from anywhere in the world. All they need is a stable internet connection. You won’t need to install new L2TP/IPsec VPN connection software, as operating systems like Windows, macOS and Linux come with built-in clients.
Delivering Cable & DSL Services
Since L2TP can securely connect to multiple points at once, internet service providers use it to deploy broadband services directly to multiple consumers simultaneously. It has proven to be quite effective for providing virtual private LAN services (VPLS) and virtual private wire services (VPWS).
VPLS provides a way to set up an ethernet-based LAN to connect devices that aren’t in the same physical area. VPWS is a tool for point-to-point communication over Multiprotocol Label Switching (MPLS) networks, which route data based on identified quick paths instead of IP addresses alone.
Additionally, ISPs with spare capacity can sell their surplus bandwidth to other providers, who can then use L2TP to route traffic from their customers without interference from the main host ISP. The IPsec encryption makes it impossible for the host ISP to see any customer information.
Setting Up Public Access WiFi
If you’ve ever wondered how the WiFi is configured at your airport or library, L2TP may have been involved. Rather than arranging individual connections for each WiFi access point, which can be overwhelming, L2TP helps organizations maintain a network of WiFi access points. A customer device can then use any of those to start a session.
Extending a Local Area Network
Companies can use L2TP tunnels to bundle various LANs, and link different branches and departments from other locations. L2TP creates a stable tunnel between the central LAN and all the remote devices.
What Is L2TP Passthrough?
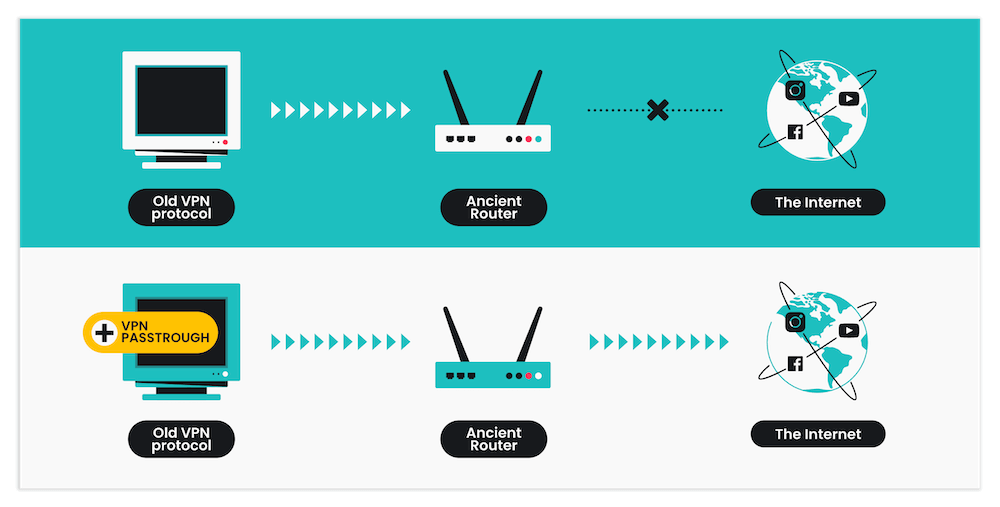
This feature allows L2TP traffic to pass through a router’s Network Address Translator (NAT) and connect to a VPN client to establish an outbound VPN server connection. NAT lets private IP networks use the internet by translating private IP addresses into public IP addresses before sending the packets to an external network.
L2TP passthrough is vital for making this happen. Without it, the router’s security settings may block L2TP traffic from reaching the intended VPN server. This is especially common on outdated routers, since most modern routers have built-in VPN passthrough features and support common VPN protocols like PPTP and IPsec.
Though it’s necessary for outdated routers, L2TP passthrough presents two problems. First, it puts strain on the CPU since all the data packets that are passing through must be encrypted and decrypted, increasing computational time. Second, enabling a passthrough can transfer vulnerabilities existing at the IP level to the central network.
What Does L2TP Use for Encryption?
L2TP gains all of its encryption through IPsec, which supports a wide range of symmetric and asymmetric ciphers. L2TP doesn’t provide any form of encryption or authentication on its own. It creates a stable tunnel between devices but lacks safeguards for maintaining data integrity.
IPsec also adds data integrity checks, which ensure that data hasn’t been tampered with during transit. There are also reliable authentication frameworks to confirm that the parties on either endpoint have authorized access.
L2TP VPN Pros and Cons
L2TP has survived for this long because it still has some effective aspects. At the same time, like any other protocol, it does have some weaknesses. Here are some of the pros and cons of L2TP.
Advantages of L2TP Connection
- Reliable security: LT2P/IPsec uses AES-256 encryption most often, which ranks among the most secure cryptographic options in the VPN industry. It’s nearly impossible for anyone to brute-force this encryption and intercept your internet traffic.
- Widespread compatibility: L2TP works with commonly used operating systems like Windows, macOS, Linux, Android, iOS and most modern routers. It can be implemented in many network setups without extensive configurations or high costs.
- Ease of use: L2TP VPN connections are very easy to set up. Operating systems like Windows even come with a built-in L2TP protocol.
- Remote access facilitation: L2TP is a key reason why companies adopt remote access for employees who work away from the central headquarters. This is because it works over the public internet, allowing them to avoid the cost of configuring a private network from scratch.
Disadvantages of L2TP Connection
- Firewall issues: Sometimes, L2TP encounters connection problems when traversing NAT gateways and firewalls. This issue is especially persistent in older routers, and you’ll need to configure an L2TP VPN passthrough to solve it.
- Speed drops with IPsec: L2TP’s speed advantages disappear when IPsec’s encryption is introduced. Your connection may become slower than usual, especially when double encapsulation is applied to your traffic.
- Vulnerability to attacks: While IPsec adds much-needed security, L2TP still has vulnerabilities. For example, CyberGhost VPN discontinued support for L2TP after discovering a vulnerability that allowed an unauthenticated remote attacker to force the targeted devices to reload.
How Does L2TP Differ From Other VPN Protocols?
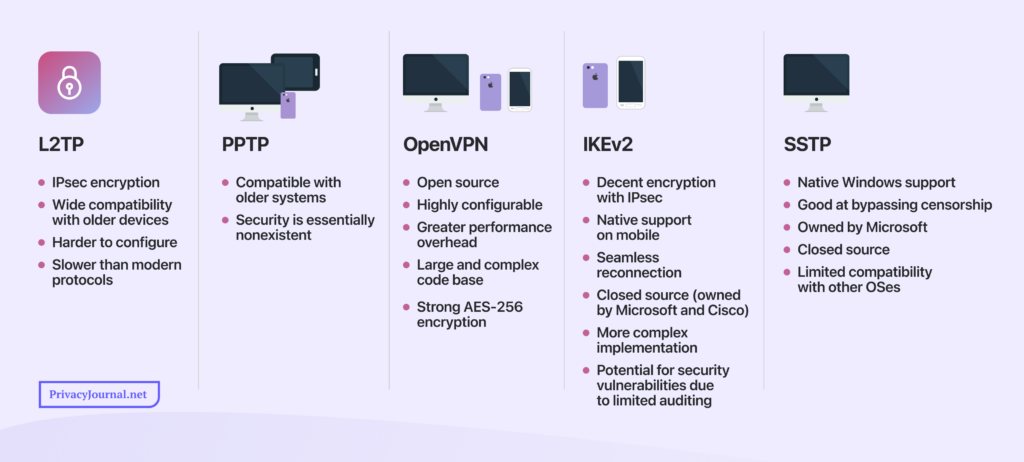
As one of the oldest VPN protocols, L2TP is rarely the best choice, falling behind IKEv2, OpenVPN and SSTP. However, it’s more secure than PPTP and most older tunneling protocols.
L2TP vs PPTP
LT2P was designed to address the flaws present in PPTP, a now-defunct protocol created for dial-up networks. L2TP/IPsec is more secure as it offers AES 256-bit encryption, while PPTP is limited to a 128-bit implementation of a Microsoft protocol called Microsoft Point-to-Point Encryption (MPPE). MPPE is now considered insecure, and PPTP is unsafe by extension.
L2TP vs OpenVPN
L2TP and OpenVPN use the same encryption standard, so you can rely on both to protect your traffic. However, OpenVPN is an open-source protocol and is less likely to be blocked than L2TP. OpenVPN can use any port, allowing it to bypass NAT firewalls without needing extra configurations.
L2TP can be blocked by firewalls unless you set up a VPN passthrough. It relies strongly on User Datagram Protocol (UDP) port 500 for IPsec to conduct key exchanges; if that’s blocked, you’ll frequently be out of luck unless you implement extra settings.
L2TP vs IKEv2
Like L2TP, IKEv2 uses the IPsec suite to exchange encryption keys over a VPN connection. IKEv2 is faster than L2TP and can quickly switch networks to reestablish VPN connections when it’s temporarily interrupted. Both protocols are vulnerable to firewall blocks.
L2TP vs SSTP
SSTP is more secure than L2TP as it uses SSL/TLS on top of AES-256 encryption, and it can bypass firewalls. However, SSTP was mainly designed for Windows devices, making it less flexible than L2TP. Furthermore, you may still need third-party software to run it effectively. L2TP is also faster than SSTP since the latter uses complicated encryption setups.
Conclusion
L2TP is trying to evolve to keep up with the rapidly changing security and privacy landscape. To sum up, L2TP must be combined with IPsec, which delivers the encryption and authentication needed to secure traffic. Additionally, L2TP works with major operating systems like Windows, macOS and Linux, making it very convenient.
However, it’s still vulnerable to firewall blocks, and it experiences slow speeds when paired with IPsec. If you don’t fancy dealing with these issues, switch to protocols that offer more options, like WireGuard.
Have you encountered the L2TP protocol when using VPNs? Did you manually configure it, or was it built into the VPN app? Tell us all about your experiences in the comments below, and thanks for reading our blog.
FAQ: L2TP VPN Security
What Is L2TP Used For?
L2TP is used to secure VPN connections, deliver cable and DSL services for ISPs, manage public WiFi networks and secure remote access networks.Is L2TP a Good VPN?
L2TP is a good VPN protocol when combined with IPsec, which makes it versatile and secure with encryption. It’s compatible with multiple operating systems.What Is the Difference Between L2TP and IPsec?
The difference between L2TP and IPsec is that L2TP is a communication protocol, while IPsec is a security protocol. L2TP depends on IPsec for security, while IPsec depends on L2TP (or another protocol like IKEv2) to send data. That’s how you get L2TP/IPsec.What Is the Difference Between L2TP and PPTP?
The main difference between L2TP and PPTP is that L2TP supports tunneling over different media, whereas PPTP supports tunnels over IP only. L2TP also works with multiple tunnels between endpoints, while PPTP works with just one tunnel at a time. Finally, L2TP works with IPsec for encryption, but PPTP uses the deprecated MPPE for security.

Leave a Reply